NYMIZ IN CANADA: DRIVING SAFE AI IN A LEADING ECOSYSTEM

In a world increasingly powered by artificial intelligence, ensuring data security and privacy has become a strategic priority. At Nymiz, we know this firsthand. Thanks to the Desafía Canada Program, we gained deep insight into the challenges, needs, and opportunities of Canada’s AI ecosystem. Canada: A global benchmark in Artificial Intelligence Canada is not only […]
HOW TO CHOOSE THE BEST DATA ANONYMIZATION TOOL FOR YOUR BUSINESS IN 2025

In an era where data privacy regulations like GDPR and CCPA are more stringent than ever, businesses must take proactive measures to protect sensitive information. One of the most effective ways to ensure compliance and security is by using data anonymization tools. But with so many options available, how do you choose the best one […]
NYMIZ AT LEGALWEEK 2025: LEADING INNOVATION IN DATA PRIVACY

From March 24 to 27, LegalWeek 2025 will bring together thousands of legal leaders, technology experts and global providers in New York to discuss the most innovative trends in the sector. This year, Nymiz is proud to participate in this benchmark event, bringing our advanced data anonymization solutions to professionals interested in improving privacy and […]
GDPR VS. CCPA: THE 5 KEY DIFFERENCES AND HOW TO SUCCESSFULLY OVERCOME THEM WITH DATA ANONYMIZATION

In today’s legal environment, ensuring data privacy compliance is a priority for businesses operating across multiple jurisdictions. Two of the most important regulations are the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States. As legal professionals in the US prepare for events like […]
PSEUDONYMIZATION: THE KEY TO GDPR COMPLIANCE AND EFFECTIVE PRIVACY PROTECTION
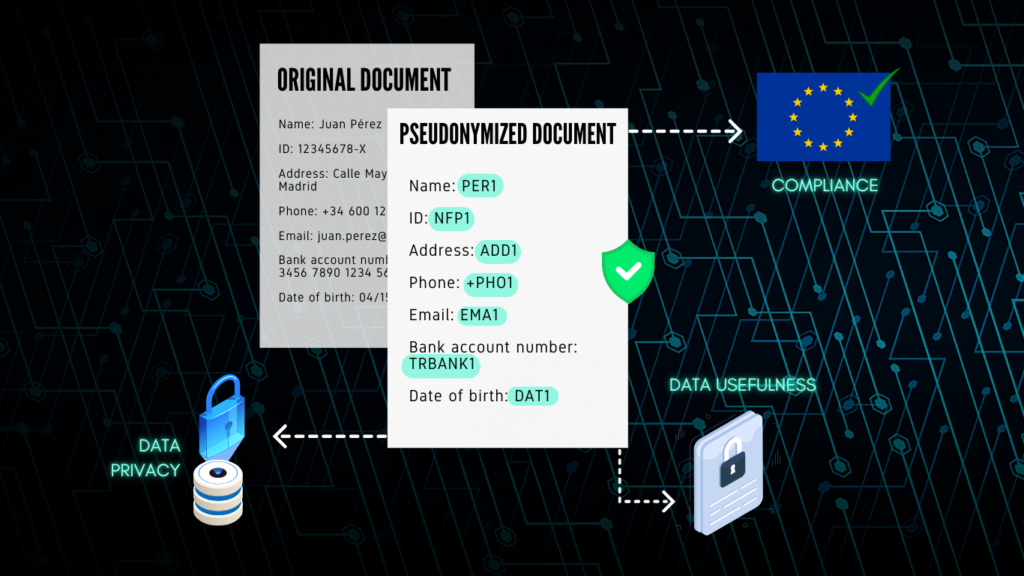
In today’s hyper-connected world, where personal data is the new “digital gold,” ensuring individuals’ privacy is a priority for both organizations and regulators. In this vein, the European Data Protection Board (EDPB) has taken a step forward by publishing new guidelines on pseudonymisation under the General Data Protection Regulation (GDPR). These guidelines not only clarify […]
LEGAL SOFTWARE TESTING: WHY SYNTHETIC DATA IS ESSENTIAL

In the legal sector, technology plays an increasingly critical role. With the growing adoption of software tools that automate legal processes, ensuring the privacy and accuracy of data used in testing has become a priority. This is where synthetic data emerges as a critical solution. What is synthetic data and why is it relevant? Synthetic […]
3 REASONS TO CHOOSE ANONYMIZATION AI IN LITIGATIONS PREPARATION

In the digital age, artificial intelligence (AI) has become an essential ally for the legal sector, redefining litigation preparation. Lawyers face the challenge of processing huge volumes of data while making strategic decisions under increasing pressure. Combining AI with advanced anonymization tools, such as Nymiz, is revolutionizing the way legal teams approach their cases, providing […]
ULTIMATE PDF REDACTION TECHNIQUES FOR DATA SECURITY IN 2025

In an era where data security and privacy are paramount, PDF redaction has become a critical process for organizations handling sensitive information. This article explores the most effective PDF redaction techniques for 2025 to ensure your organization stays compliant and secure. What is PDF redaction? PDF redaction involves permanently removing or concealing sensitive information from […]
WHAT IS UNSTRUCTURED DATA IN HEALTHCARE AND HOW TO PROTECT IT?

The healthcare industry handles an immense amount of critical information ranging from medical records to diagnostic images, emails, and test results. However, a large portion of this data is not organized into structured databases; it is what we call unstructured data. In a previous article, we explored the importance of protecting unstructured data in general. […]
KEYS TO PROTECTING YOUR COMPANY’S UNSTRUCTURED DATA

In a world where technology is advancing at a dizzying pace, protecting unstructured data has become a priority challenge for businesses. This data, which includes emails, images, videos, documents, and more, represents a large proportion of the information that organizations handle. However, its messy and complex nature makes it extremely difficult to protect. Why is […]

